How to enforce SafeSearch using Pi-Hole
If you have deployed Pi-Hole on your network, then you can enforce safe search using your Local DNS server.
This article explains how to do just that for Google, Bing, DuckDuckGo and YouTube.
This will affect all the devices connected to your network and using your P-Hole as DNS server. (Changing the DNS servers on your router)
This will not impact devices which have had the DNS servers manually set to an external provider.
There will be other ways of achieving the below, but I like knowing exactly what my setup is and manage it as required.
Getting the IP Addresses of the safe endpoints (safe_sites)
The first steps will be to gather the IP Addresses for the safe endpoints, to do that you run a “nslookup” for each of the “safe_sites”, use either CMD or PowerShell as shown below;
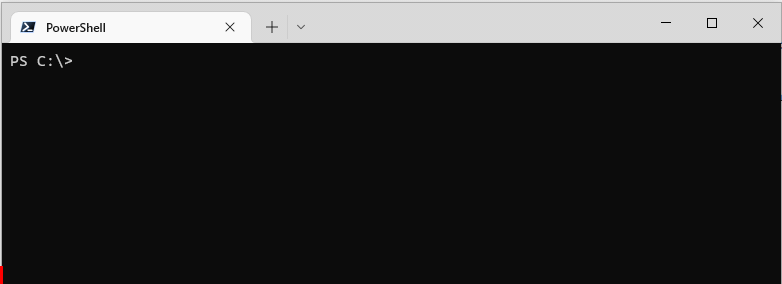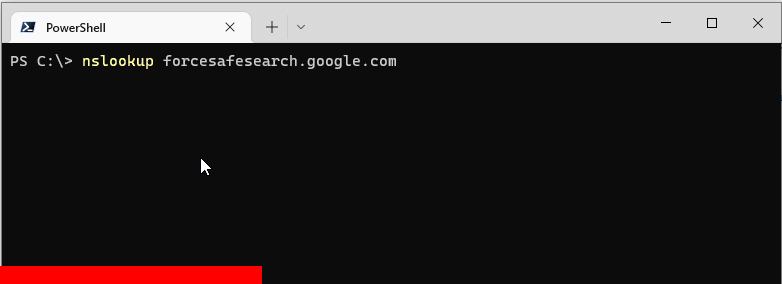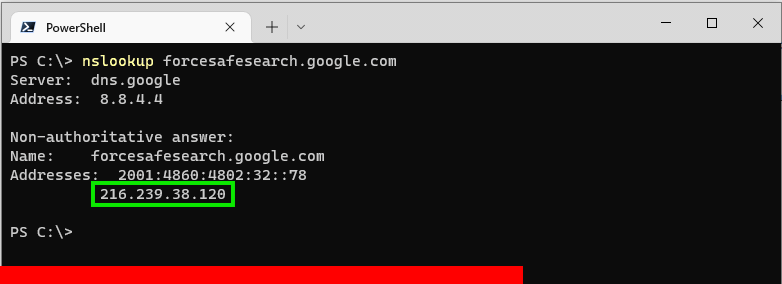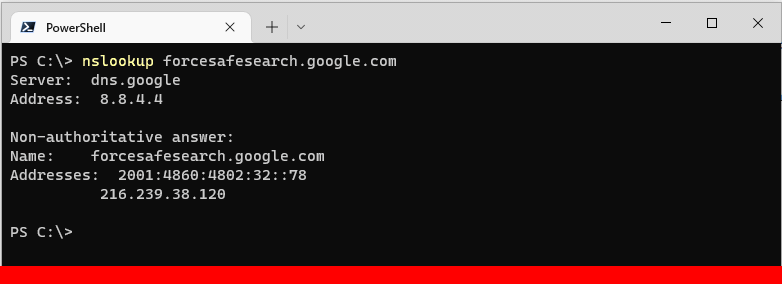
The above “nslookup” results in an IP Address, keep note of that, then do the same for the other “safe_sites” you may use.
Below is a list of those covered in this article (these were correct at the time of writing):
google:
safe_site: forcesafesearch.google.com
ip: 216.239.38.120
youtube:
safe_site: restrictmoderate.youtube.com
ip: 216.239.38.119
- OR
safe_site: restrict.youtube.com
ip: 216.239.38.120
bing:
safe_site: strict.bing.com
ip: 204.79.197.220
duckduckgo:
safe_site: safe.duckduckgo.com
ip: 52.142.126.100Adding the above as DNS records in Pi-Hole
In Pi-Hole go to the dropdown “Local DNS” and click on “DNS Records”, then add the respective “Domain” (safe_site) and “IP Address” pairs as below;
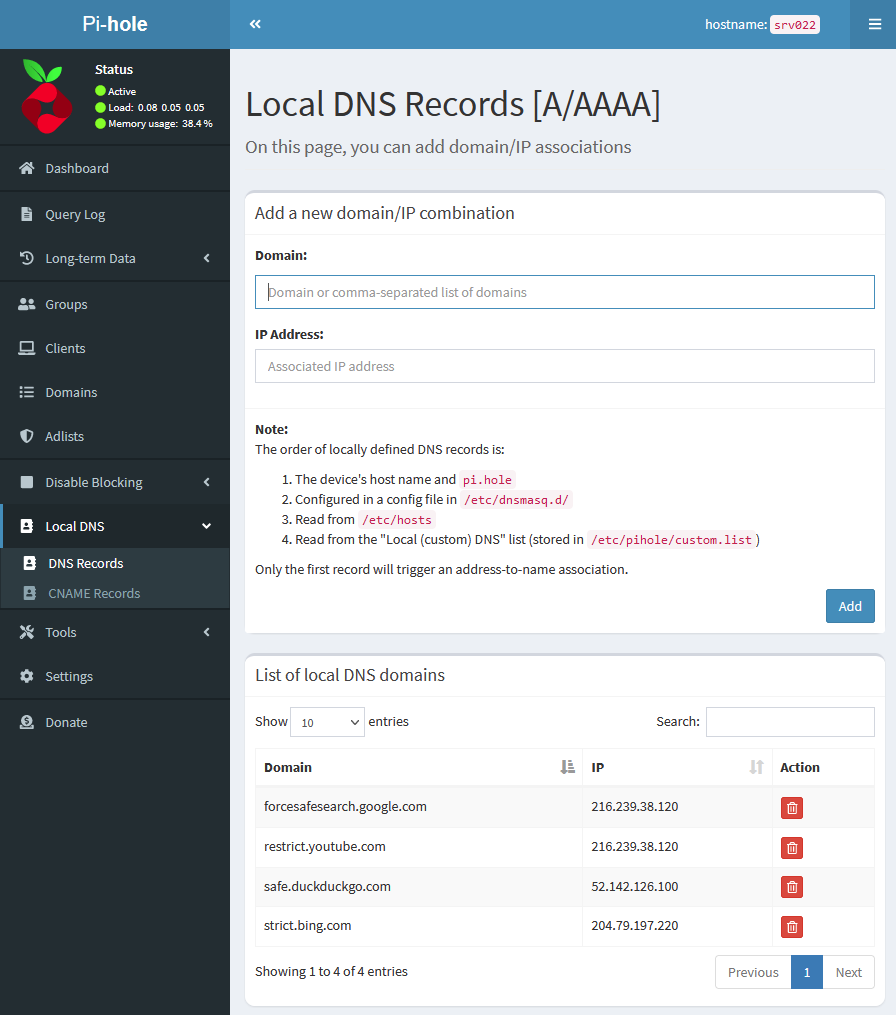
Force the Search engines to resolve to the safer/strict endpoints
Now you can redirect any domains to the safer endpoint configured above by configuring “CNAMES”.
For each search engine you want to force Safe Search on, you create a “CNAME” record pointing to the respective “DNS Record”.
The example below redirects “google.com” to “forcesafesearch.google.com”.
You need to configure “CNAMES” for all other Google domains used, such as “google.co.uk“, “google.de“.
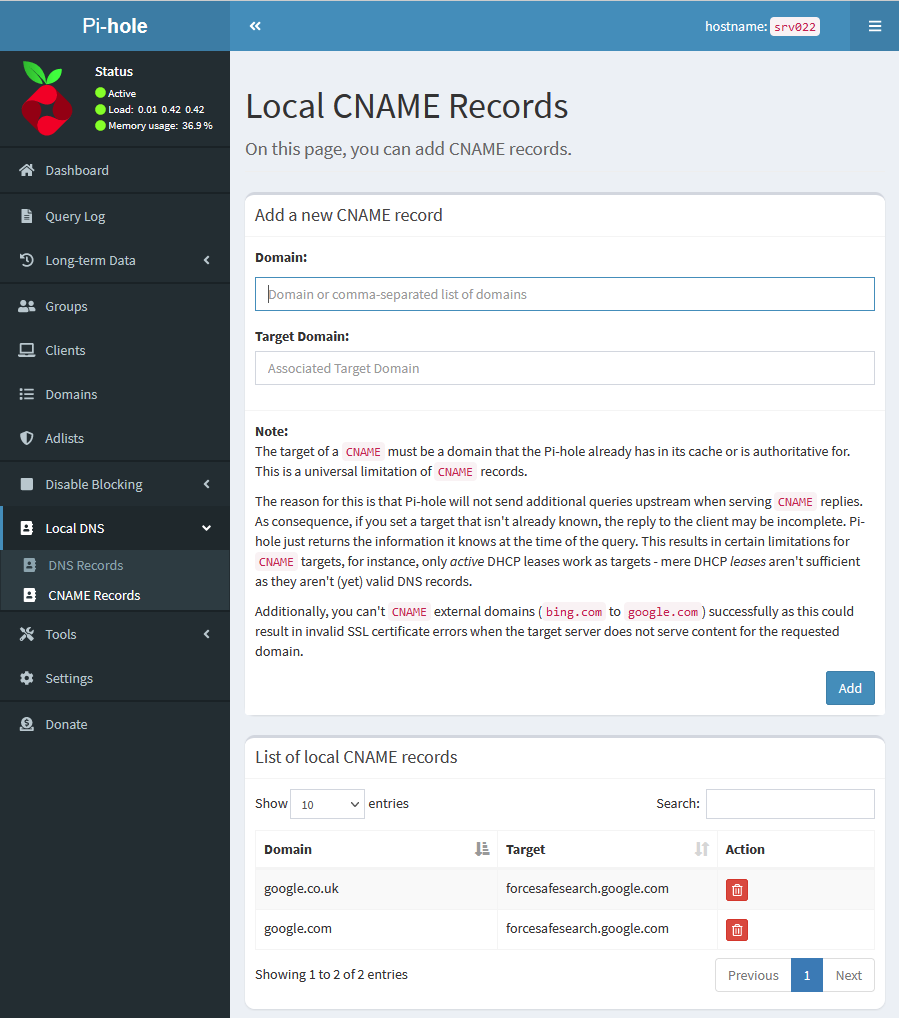
The same as above would go for “Bing” and “DuckDuckGo”, as below;
While “Bing” only needs one “CNAME” record, “DuckDuckGo” has a couple more, as for “YouTube”, there is a larger list of “CNAMES” required.
google:
safe_site: forcesafesearch.google.com
ip: 216.239.38.120
cnames:
- google.com
- google.co.uk
- google.de
(or any others you require)
youtube:
safe_site: restrictmoderate.youtube.com
ip: 216.239.38.119
- OR
safe_site: restrict.youtube.com
ip: 216.239.38.120
cnames:
- www.youtube.com
- m.youtube.com
- youtubeei.google.com
- youtube.googleapis.com
- www.youtube-nocookie.com
bing:
safe_site: strict.bing.com
ip: 204.79.197.220
cnames:
- bing.com
duckduckgo:
safe_site: safe.duckduckgo.com
ip: 52.142.126.100
cnames:
- duckduckgo.com
- duck.com
- start.duckduckgo.comBut does it work?
Assuming all was done as above, a search using Google should result on the below;
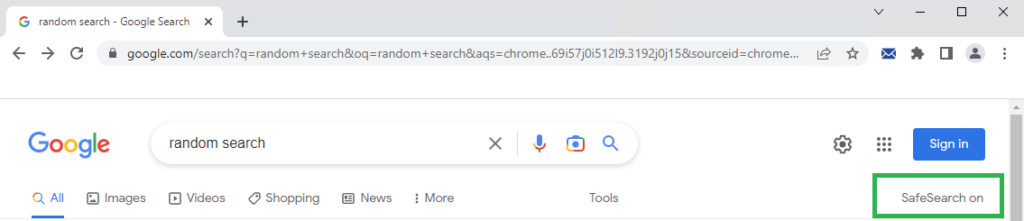
And if you click on “SafeSearch on” to try and disable it, you should see the below;
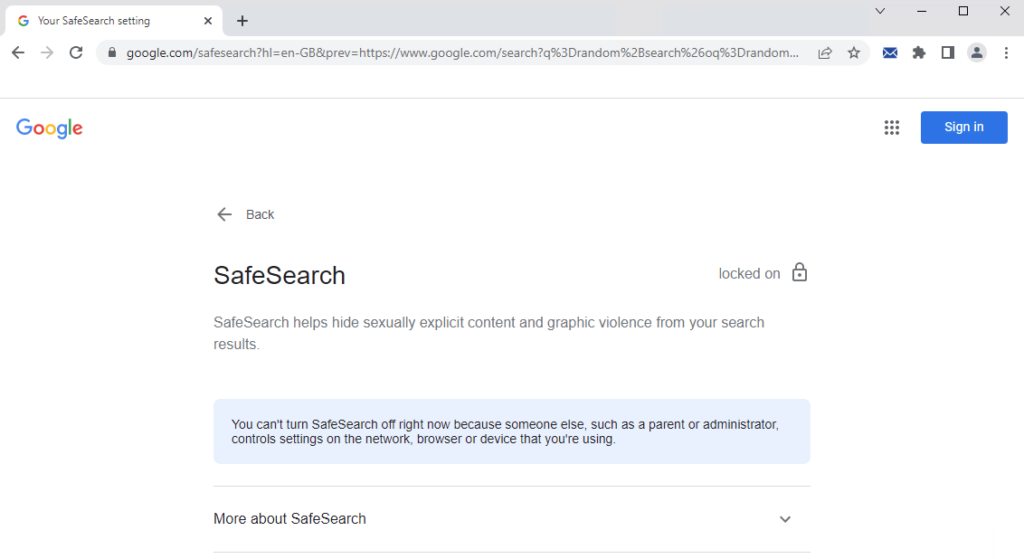
As for YouTube;
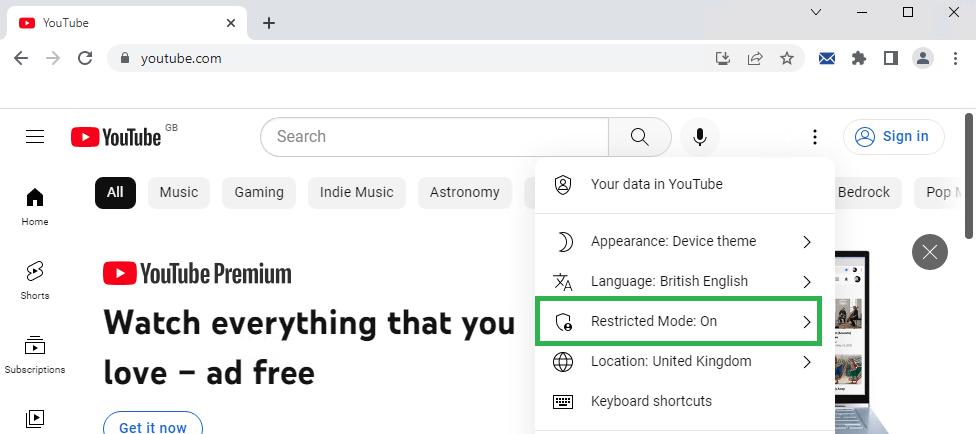
And you should also be unable to disable it, I can confirm this to work with the mobile apps as well.
To achieve the described above, you need to have completed the below (or similar setup);
Installing Pi-Hole on Ubuntu 22.04
Changing the DNS servers on your router
Using Pi-Hole on the go with OpenVPN

Hi there. Thank you for the tutorial. I do feel compelled to comment as I’m facing some issues I cannot resolve. I’ve setup pi-hole with the DNS records and CNAMEs but the rule is not being enforced in my network. I’ve pinged the domains and I’m getting the correct IPs but any device in my network can just turn safe search off. I had to edit my kid’s /etc/hosts file to make it work. Do you have any idea of how to resolve this in the network level?
Not sure how technical you may be, but, to be changing the hosts file, fairly os my guess.
Your kids device, is it running Linux?
The only reasons I could think it not working would be either 1 of the below:
– Not using Pi-hole as the DNS server
– Browser cache not cleared
Let me know if you tried above please..
Yes, his device is running a Linux Mint and browsing is done over Firefox.
When I ping http://www.google.com in the terminal I get a reply from IP 216.239.38.120, as expected.
DNS is being served from my router, with the following settings in an Asus router:
– WAN DNS Setting
– DNS Server: Assigned to IP of local machine running pi-hole.
– Forward local domain queries to upstream DNS: No
– Enable DNS Rebind protection: No
– Enable DNSSEC support: No
– Prevent client auto DoH: Auto
– DNS Privacy Protocol: None
I’ve disabled Firefox’s DNS over HTTPS and cleared the browser’s cache and it still didn’t work.
Only after editing /etc/hosts safe search started being enforce. Not ideal, as I’d like any device in the house to be locked to safe search.
Kids will use any device they can get their hands on. XD
I’ve also checked over my phone (iOS device) and safe search is also not enforced in it when in network.
However, I’m not sure the latter would work on a phone anyway, as it seems apple has other DNS routes for the phone.
OK,
If you do a “dig google.com” on the terminal, what does it show as “SERVER:”, just below “Query time”?
Ref: “https://phoenixnap.com/kb/linux-dig-command-examples”
In theory it should show you the IP of you pi-hole..
Thank you again for helping with this. The DNS server is listed as a local machine address, not sure why. Please see output below:
; <> DiG 9.18.18-0ubuntu0.22.04.2-Ubuntu <> google.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 33654
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 65494
;; QUESTION SECTION:
;google.com. IN A
;; ANSWER SECTION:
google.com. 0 IN CNAME forcesafesearch.google.com.
forcesafesearch.google.com. 0 IN A 216.239.38.120
;; Query time: 92 msec
;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP)
;; WHEN: Wed Feb 28 07:16:07 MST 2024
;; MSG SIZE rcvd: 85
Hi again, little busy lately…
Have done some testing, and have been able to get Chrome to ignore the DNS settings by doing as below:
Go to Chrome “Settings -> Privacy and Security -> Security” find “Encrypt the names of sites you visit” and enable it, once enabled, this allows you to “Select DNS provider” and if not set to “OS default (when available)” it would use whichever DNS provider selected.
The options would be to keep it enabled, and ensure that “OS default (when available)” is selected, or disable “Encrypt the names of sites you visit”.
Try that and let me know if it works as such for you.
I’ve just implemented this on my device, but I’m trying to understand the logic of adding the DNS records? Wouldn’t they already by picked up by Pi-Hole and therefore you only need to add the CNAME’s to Pi-Hole to do the forced redirects?
Hi,
Afraid not, if you just redirect “google.com” to “forcesafesearch.google.com” you will probably be server a “404. That’s an error.” (this from memory).
You could probably get set each of the CNAMES as DNS records, and point them directly to the respective IP’s instead (not tested), but as described, (to me at least) makes it easier, as DNS records do not change, and you can point any CNAME record to the respective DNS record.
Hope the above makes sense, but if you find an easier way to configure it with the same results, I’d happily update the article.
Hello,
I followed the above steps, but only Bing and Google work. Duckduckgo does not. It forces the SafeSearch to Moderate, but even if I change it to off or strict it will keep at Moderate, but the issue is that it still pulls adult sites like porn.com
Any ideas?
Thanks.
Hi,
I have just tested, and can confirm that “DuckDuckGo” settings show as moderate, but, when I do a search, the results are in fact restricted, with no results shown.
Mind testing again? I seem to get the expected results!
When searching, I get “No results found for xxxx.”
But when you browse using ipv6 this doesn’t work
Hi Rob,
Thank you for reaching out.
All the articles published are tested on my own network, have not had any issues with IPV6, neither have I realized that it didn’t work when using it. This is, however, due to having disabled IPv6 on my home network, which I don’t yet take seriously due to the many issues I’d have with other configuration (i.e Cloudflare).
Maybe not an option for you, but perhaps you could disable IPV6 as well, depending on your router?
A TP-Link, as my own, would allow you to do that fairly easily.
Step 1 – Navigate to the IPv6 Support tab menu -> IPv6 Setup
Step 2 – De-Select the Enable IPv6 checkbox
Step 3 – Save Settings
Step 4 – Reboot Router
If you want to disable IPv6 on a specific machine, assuming it to be on Windows here, I would use PowerShell as below:
$adapters = Get-NetAdapterforeach ($adapter in $adapters) {
$adapterName = $adapter.Name
Disable-NetAdapterBinding -Name $adapterName -ComponentID ms_tcpip6
Write-Host "IPv6 disabled for adapter: $adapterName"
}
Save the script with a .ps1 extension (e.g., disable-ipv6.ps1). Then, open PowerShell with administrative privileges and navigate to the directory where the script is saved using the
cdcommand.Execute the script by typing
.\disable-ipv6.ps1and pressing Enter. It will loop through all network adapters and disable IPv6 bindings on each one. The script will display a message for each adapter where IPv6 has been disabled.Hope that helps